

This part of the research into the bizarre happenings in the 2016 Presidential Election campaign is continuing after evidence was found that verifies a Stand Down Order was given to the Incident Response team from Crowdstrike, the cybersecurity company hired for the DNC to eliminate the hackers from the DNC's network in 2016. The evidence verifying the Stand Down Order was found in the 2017 book Hacks, written by former DNC executive, Donna Brazile who is now a contributor to FOX News, providing commentary on some news shows and serving as moderator for some of the panel discussions.
Before drilling further down into the existence of this Stand Down Order, let's take a further look into the alleged Russian "hacker groups" involved in the alleged hack of the DNC in 2015 and 2016. We will have to define and discuss some hacker and cyber security terms as part of this review.
Two alleged Russian hacker groups are said to have breached the DNC network. These two hacker groups are called Advanced Persistent Threats (APT). This term can be a bit confusing since APT are frequently identified by the types of malicious software (Malware) each APT uses. These tools appear to be the bigger threat, as the hackers behind them could not function without them, so it makes more sense to describe these tools, that are embedded on the target network's servers, workstations, laptops, etc. and enable the hackers to operate in the network as virutal users as being THE APT. However, the experts do not call these tools--the Malware--the APT. The people using the tools are the APT. APT are frequently given nicknames. The two nicknames that are of interest to this saga are FANCY BEAR and COZY BEAR. We will discuss them in the order of the timing of their alleged penetrations of the DNC network.
Cozy Bear is described as follows by Wikipedia:
"Cozy Bear, classified as advanced persistent threat APT29, is a Russian hacker group believed to be associated with Russian intelligence. The Dutch AIVD deduced from security camera footage that it is led by the Russian Foreign Intelligence Service. Cybersecurity firm CrowdStrike also previously suggested that it may be associated with either the Russian Federal Security Service or SVR. The group was given other nicknames by other cybersecurity firms, including Office Monkeys, CozyCar, The Dukes..."
Cozy Bear was alleged to have breached the DNC in the summer of 2015. That's right, the year before the Presidential Election. The alleged Russian Intelligence hackers stayed on the DNC network, off and on, for nearly an entire year without ever being discovered by any of the DNC's IT staff, or consultants hired to try to find the alleged Cozy Bear hackers.
Part of this failure by the DNC to find these hackers was the lack of any kind of robust assistance by the FBI. One Special Agent was assigned to telephone the DNC and inform them that a Russian government hacking group, called "The Dukes," were on the DNC network. During the late summer and early fall of 2015, such telephone calls were the only attempts to galvanize the DNC into action. The problem was that the DNC employees, and consultants like Yared Tamene, who had the most early contacts with the FBI, could not find any evidence that Cozy Bear--"The Dukes"--were in the network. These Russians were trying very hard not to be detected. The second bunch, as we will see, didn't try to hide their presence on the DNC network.
For some reason the Russians forgot how the Chinese intelligence hackers got caught hacking the Obama campaign in 2008. The National Security Agency detected them and alerted the FBI. Crowdstrike handled that incident response as well, and it was well-publicized. Such publicity is called "public shaming" and was a key element in US response to state sponsored hacking. The problem is, some regimes don't care if the United States says something embarrassing about them. If the hacking works for them, they won't quit until you make them quit. The important thing is, the story got enough play that it is very likely Russian intelligence agencies knew that the NSA could trace their transmissions of data back to home base as was done to the Chinese intelligence hack of the Obama campaign. One has to wonder why Cozy Bear did something as dumb as send a transmission directly to their headquarters in Moscow which the NSA discovered. More on this in another chapter as Dutch Intelligence had hacked an SVR office security camera system. What is said to have been found there is very interesting and may provide a clue as to why we have experienced all these strange incidents during and since the 2016 election.
At any rate, FBI Director James Comey did almost nothing while alleged Russian intelligence hackers ran barefoot through the DNC network for nearly an entire year. Comey claimed that the DNC would not allow Comey to send people into the DNC headquarters to ferret out the hackers, so he just had the one agent make phone calls and hold a couple of meetings with DNC executives. Nothing much happened as a result while alleged Russian hackers pranced around through all of the servers, and most of the workstations, inside the DNC network.
This is odd behavior for Comey, who frequently utilized National Security Letters for far lesser reasons. I used to say that Comey would issue a National Security Letter when someone's cat got stuck up a tree, but that is probably an exaggeration. National Security Letters have the power of search warrants, but do not require the signature of a federal judge or magistrate. How ofen did Comey issue National Security Letters in the past? Try this complaint by Comey published by the group LAWFARE on their blog dated January 9, 2014:
“What worries me about their suggestion that we impose a judicial procedure on N.S.L.’s is that it would actually make it harder for us to do national security investigations than bank fraud investigations,” Mr. Comey said. He added, “I just don’t know why you would make it harder to get an N.S.L. than a grand jury subpoena,” calling the letters “a very important tool that is essential to the work we do.”
Here LAWFARE describes the reasons for Comey lamenting about changes to the issuance of NSLs as follows:
"Such letters have long been used in bank fraud and other cases, but their use exploded over the past decade as they were expanded to terrorism investigations, with the agency now issuing tens of thousands a year since Congress lowered the legal standard. The review panel urged Mr. Obama to require a judge to find 'reasonable grounds' that the information sought 'is relevant' to terrorism activities.
See? Mr. Comey issued "tens of thousands" of NSLs every year. At least he did until alleged Russian spies started lounging around in the Democratic Pary's main computer system for an entire year. For some inexplicable, and probably bizarre, reason, Comey took a casual, laid-back response. It was like he could care less Russian spies were logging onto the Democratic Party's main computer network on a daily basis. Maybe bank thieves are more important than Russian spies inside a computer system, accessed by Members of Congress and the Senate who belong to the Democratic Party, who also have access to highly classified information. Well, I'm just not the expert that Comey is, I guess. That is why I can't see why Russian spies occupying the DNC network, like homeless guys camping out on a Los Angeles street, is just nothing about which to get excited. It must be that you have to be James Comey to understand all of this.
This won't be the last time Comey appears in this story to do something inexplicable, but significant, in creating the world in which we live now. Comey played a major role in the emails being stolen by not intervening to stop the alleged Russian hack of the DNC.
Wikipedia intoduced APT 28, Fancy Bear, this way:
"Cybersecurity firm CrowdStrike has said with a medium level of confidence that it is associated with the Russian military intelligence agency GRU."
Medium confidence in an assessment like this is not all that robust. Of course, High Confidence is much better, and proof beyond any reasonable doubt is a better target yet. Crowdstrike has medium confidence, but that medium confidence is dead certainty for most of institutional Washington, DC. When both the Democratic and Republican parties agree to something publicly, that something is very special. Both parties agree that Fancy Bear stole the DNC emails. The hackers were Russian military intelligence operators, the GRU.
The funny thing is, the DNC caught on to the Fancy Bear group within about three weeks. APT 28 was about as covert as Moe, Larry, and Curly trying to fix some rich guy's plumbing. There was one giveaway after another by this bull-in-a-china-shop group of Russian hackers. They got in sometime in late March 2016. While unbeknownst to Fancy Bear, Cozy Bear was enjoying the easy pickings for some 11 months before them with the same DNC crew unable to find any evidence that there were Russian hackers logging on to their network every working day for a year. DNC computer security consultant Yared Tamene stopped returning the FBI's calls about Cozy Bear because he found no evidence that anyone had hacked the DNC network let alone Russian spies. That sure wasn't the case with Fancy Bear. As Donna Brazile described Fancy Bear's activities on Page 138 of Hacks:
The reader will be asked to remember that the same DNC IT employees failed to find evidence of any hack during the time in 2015 when they were looking in vain for the Cozy Bear hackers inside the network. Fancy Bear they found in just a few weeks, and prior to any compromising emails being created and stored on the DNC network.
The problem with all the obvious flares the clumsy GRU hackers threw up, and all the bread crumbs left behind for Crowdstrike to follow that gave their "secret identities" as Russian spies away, Fancy Bear had a very covert mission. Fancy Bear had to get Donald J. Trump elected by stealing embarrassing emails from the DNC and giving them to Wikileaks. If Fancy Bear gave away both their presence, and the fact they were professional Russian GRU spies as well as hackers, the whole covert operation would be compromised. The entire world would know that Vladimir Putin wanted Donald Trump in the White House. Such a revelation would incense most Americans, including the old anti-Soviet conservatives from the defunct Cold War, and cause them to, perhaps, reject Donald J. Trump as being a "puppet of Putin." "Putin's Puppet," Donald Trump, could likely be defeated if the Russian help for his campaign was revealed. Fancy Bear hackers responded to this need for secrecy by doing all they could, according to Ms. Brazile's eye witness recollections, "to be found out."
Fancy Bear was caught. Not even wearing Groucho Marx mustaches as they hacked would keep them from being exposed and later indicted by Mueller. The Russian spies even found out Crowdstrike was observing their activities, but continued operating even though Crowdstrike's presence had to mean Putin's alleged plot to help Trump get elected by stealing DNC emails and publishing them was already doomed to be exposed.
It would be obvious for observers of all this to expect Hillary Clinton and the Democrats to use this hack against Donald Trump in the campaign, and accuse Trump of possible treason. In fact, this kind of rhetoric was heard frequently from Democrats campaigning for Hillary Clinton through October and the first week of November. Such accusations from Hillary Clinton, that Trump was working with Putin to steal the election, were liberally used throughout the last Presidential debate. This will be important to remember as we develop the plausible scenarios that could explain what really was going on during all of this.
Again, remember that Fancy Bear could not afford to get caught as that would expose the Russian government as being behind the DNC hack which would be followed by attacks by the Democrats that Donald Trump was some kind of asset of the Kremlin. These attacks were made during the campaign, and in the last debate, as a result of Fancy Bear being allegedly detected on the DNC network.
Fancy Bear did a lot to expose themselves. As pointed out in Part 13, the Mueller indictment tells us Fancy Bear detected Crowdstrike on the DNC network on, or before, May 31, 2016. Fancy Bear stole the first round of emails on May 23, 2016 and May 25, 2016, but continued operating into July 2016 after finding a way to get back into the DNC network after Crowdstrike kicked them out in June. Even after discovering Crowdstrike's presence in the DNC network, the alleged GRU hackers kept going into the DNC network. They had to know the covert operation to "elect Donald Trump" was blown completely, but they continued to operate for the willing spectators from Crowdstrike, who did nothing from May 31, 2016 until June 11, 2016. Crowdstrike finally took action to remove the alleged Russian hackers during the weekend of June 11 and June 12, 2016, the same weekend as the Orlando Pulse Nightclub mass shooting. The Pulse incident pulled most of the media coverage away from the DNC hack all during the following work week.
Another thing to remember, as we develop the plausible scenarios, is that the first description of the hack that was given to the Washington Post, by executives of the DNC and Crowdstrike, on June 13, 2016 did not identify the emails as having been stolen. Only two files of opposition research about Donald Trump were stolen by the alleged Russian spies. Emails were only "read/monitored" by Fancy Bear. That was a different hack than the one we were sold later, and believe firmly in today.
In the most recent part of this series about the bizarre events of the 2016 Presidential Election, we revealed how the DNC emails were stolen. More detail of that will be provided in this part, including a breakdown of the illicit downloads of the DNC emails and a summary of the ten inboxes looted during the incident.
The cybersecurity firm that responded to the DNC incident was Crowdstrike. We assessed that Crowdstrike was ordered to Stand Down and do nothing to stop the looting of the DNC network. I did not name a definitive source of the Stand Down Order, but surmised that a "high echelon of power" gave the order. This analysis was controlled by the assumption that the DNC management would not want any of their data to be stolen by any hackers, let alone any Russian government hackers, especially in a Presidential Election year. That assumption was found to be in error.
In her 2017 book, Hacks, Donna Brazile informs us on Page 137:
"In May (May 6, 2016--GJ), when Crowdstrike recommended that we take down our system and rebuild it, the DNC told them to wait a month, because the state primaries for the presidential election were still underway, and the party and the staff need to be at their computers to manage that effort."
So, according to Ms. Brazile, "the DNC," meaning DNC executives, told Crowdstrike to stand down and do nothing to stop the hackers from exfiltrating DNC emails and other documents from the network, including donor information.
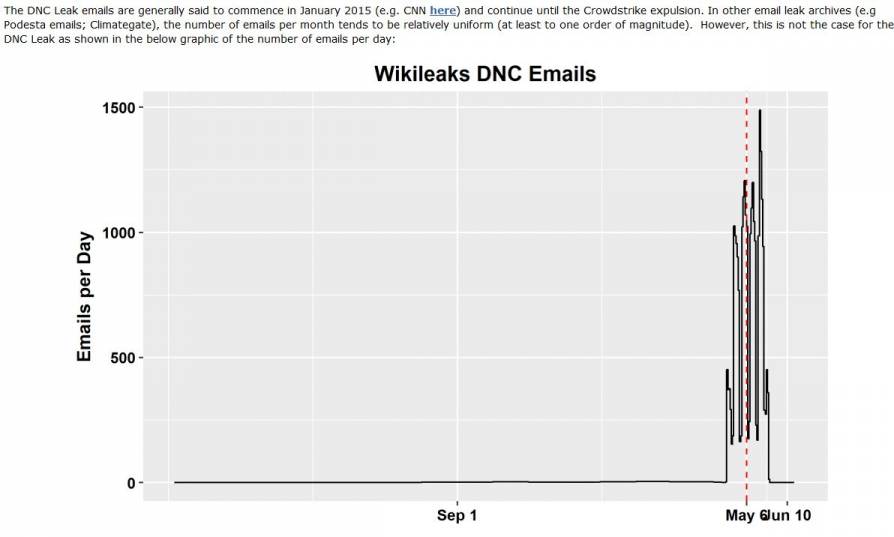
As we saw in an earlier part of this series, email volume at the DNC exploded after Crowdstrike arrived on the network. The volume stayed well above normal levels well into June. All the damaging emails, about the alleged cheating of Bernie Sanders and an alleged money laundering operation, appeared during this exact time period. As pointed out in our most recent chapter to this story, somehow this change in email volume was not noted by the Russians as something that aroused their suspicion. Later that month, the alleged Russian hackers, all of whom were alleged to be agents of the GRU, Russian military intelligence, were running Internet searches about Crowdstrike. According to Mueller's indictment of the 12 Russian names, Crowdstrike was discovered by the alleged Russian hackers to be on the DNC network watching them.
One would wonder why these seasoned GRU agents didn't think the sudden email surge was a collection of fiction, created strictly for their benefit by not only Crowdstrike, but also the FBI, since Shawn Henry, former cynlbercrimes executive with the FBI, manages Incident Response Engagements for Crowdstrike.
As we saw above, Donna Brazile explained the reason for the Stand Down Order as being the need for the DNC personnel to stay on their computers until the state Presidential primaries were over. Crowdstrike would have to wait 36 days to finally change out the DNC network's machines, and disconnect from the Internet temporarily, in the first attempt to get the alleged Russian hackers off the network. Did Crowdstrike really have to wait 36 days? I found a schedule of the Presidential state primaries to determine if there was reasonable time to perform such an operation in days between primary votes. Below is a chart showing the timeline of the state primaries.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
First thing to remember the first tranche of emails exfiltrated from the DNC were taken on May 23, 2016 and May 25, 2016. Let's see how many days were available to do this work from May 7, 2016 and May 23, 2016. May 7, 2016 was the day after Fancy Bear and Cozy Bear were allegedly identified by Crowdstrike.
On May 7, there was a primary on the US territory of Guam, but not another one until West Virginia's primary on May 10, 2016. That provides at least three days without a primary, which are not many, but something could still be done, such as the reimaging, or replacement, of laptops carried by some of the employees. Other operations could be done while waiting for a longer lull in the primaries. Performing these operations in between May 7 and May 10 would mean fewer things would need done during a longer period.
Between May 10's West Virginia primary and the primaries in Kentucky and Oregon on May 17 are seven days. Here is a reasonable number of days before the emails were exfiltrated to complete all of the technical steps that would not get done until the weekend of June 11, 2016 and June 12, 2016, plus training for the employees.
After the May 17, 2016 Oregon Primary, there are five days left to eliminate the hackers to avoid the May 23, 2016 download of the ten DNC inboxes looted by the data thieves. After that, there is no sensitive data left to protect that hadn't been looted by the UNKNOWN SUBJECTS.
In my opinion, there was no need for the DNC to wait until after all the primaries to get the Russians off the network. There were enough days without primaries, 10 days, to get most of the corrections to the DNC network completed. Like Michael Sussmann's claim that Crowdstrike had to go slow in response to the alleged Russian hackers, in order to protect the system logs from being deleted by the "Russian hackers," the argument that the DNC had to wait until after all the state primaries were over to get rid of the alleged Russian hackers simply does not hold water.
In addition to the 10 days when there were no primaries being held in May, there were alternatives the DNC had available to maintain communications during the primaries while the network was being rebuilt. Email services could be contracted for emergency email service, which could be publicized on the DNC network. Fax machines could be utilized. The phone system would have to be changed, as the DNC was using Voice Over Internet Protocol (VOIP), which was on the same network that was allegedly hacked by the Russians, but this was Washington, DC. Some kind of emergency telecom system could have been arranged during one of those lulls in primary coverage. The public could be alerted of the changes on the DNC Web site in real time.
Even if they left the hackers on the network, they could have taken steps to make life harder for them, such as wholesale password changes for all employees and the encryption of the database of passwords. Email regulations could include restrictions on the sending and receiving of any potentially embarrassing email, and a requirement to save emails by printing out the emails and filing the paper copies rather than keeping the electronic versions which would all be deleted immediately after printing them out.
There were very simple things that could have easily be done to keep the emails from being stolen. The decisions that were made resulted in the following:
1. The theft of the emails was made inevitable and unstoppable.
2. The publication of the emails was also made inevitable simply by making them available for theft, with no steps taken to prevent the theft, and no effort to eliminate the danger of compromising emails being stored on the system for the thieves to steal. As noted in an earlier part of this report, "No one can steal what they do not know exists."
As we study the possible real reasons these decisions were made, it is instructive to remember this old dictum in American legal philosophy:
"It is reasonable to assume that one intends the natural consequences of one's actions."
I think it is also reasonable to include "the natural consequences of one's INactions," as well as their actions.
The big lesson learned from this is the following:
"It does not matter who stole the emails and made them available to Wikileaks. It could have been the Russians, DNC executives, the Hillary for America campaign organization, the FBI, Crowdstrike, DNC employee Seth Rich, or some combination of several, or all, of them. No one was going to steal those emails without the DNC executives and Crowdstrike permitting the theft to take place while knowing exactly who the thief was, or the thieves were, and how they managed to perpetrate the theft."
That is the fact that has been hiding behind all the political and media smokescreens from the very beginning of this--this--THING, whatever it really is. And it was hiding in nearly plain sight this entire time.
We will go over possible scenarios to explain why, and how, all of this might have happened in the next installment. After the next one is completed, we will finally address Seth Rich, and how likely it is that Seth Rich stole the emails and sold them to Wikileaks, before doing a final summary section to finish this DNC Hack story for good. We have a lot more to cover than this alleged hack, and have been researching most of those topics while researching the hack story, so we have some of that work done already.