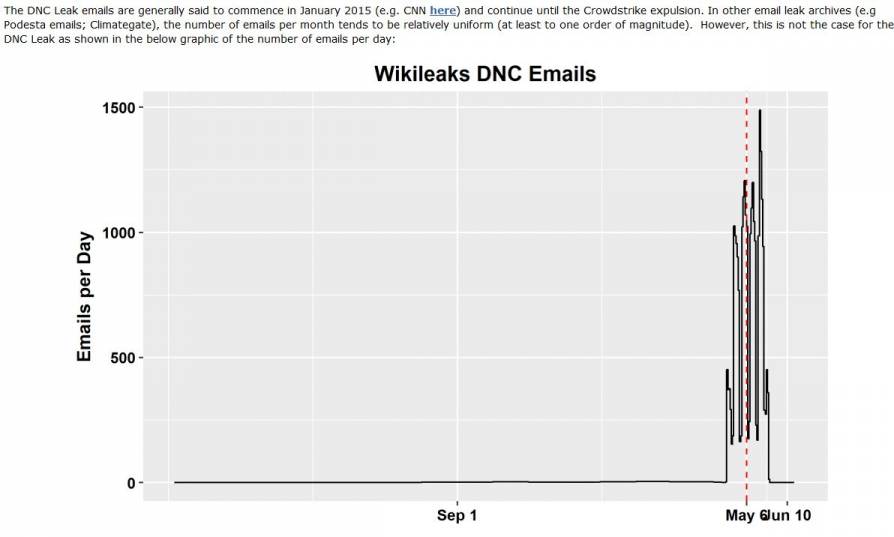
"In fact, more emails were hacked after Crowdstrike's discovery (of alleged Russian hackers) on May 6 (2016) than before. Whatever actions were taken by Crowdstrike on May 6, they did nothing to stem the exfiltration of emails from the DNC."
I keep telling everyone that I am done with the alleged DNC hack, which I am sure many of you know I do not think was necessarily a hack, but new information keeps getting discovered. In the case of Steve McIntyre's blog, new information is not quite new. McIntyre's work has been out there for nearly a year now. The strange thing is, at least three of us, independently looking at how Crowdstrike performed the Incident Response engagement at the DNC, were inspired to use the LIFELOCK commercial about the "Security Monitor" who is not a "Security Guard" as a meme to represent what Crowdstrike did on that engagement. I didn't get the idea from the other two bloggers, and they didn't get it from me. Mr. McIntrye beat me by about four months or more. The idea was just that obvious that the LIFELOCK commercial perfectly fits how Crowdstrike operated at the DNC. There was never a reason that any of the emails should have been stolen, or at least none of the really damaging ones written between April 19, 2016 and May 25, 2016, the last date of an email in the Wikileaks DNC archive. The loss of the damaging emails were the result of Crowdstrike not containing the hack. We will now look at the nature of the DNC Email Archive and take a look at what that archive of emails can tell us about the nature of the theft, and the likelihood that certain named suspects, such as "Russian Hackers" and Seth Rich, the DNC employee widely reputed to have been the source of the emails to Wikileaks, were responsible. We will address the allegations against both Russian intelligence and Seth Rich in separate articles in the DNC Hack section of this election blog. Hopefully, that should put this section of this election analysis to rest until a formal investigation provides the final answers. There should be a complete, formal investigation into what actually happened, too. Not opinion, theory of "intelligence assessments," but an empirical, factual investigation without any partisan or ideological bias. Who can do that today is anyone's guess. This should be a probe into crime, not the practice of politics by other means.
As Steve McIntyre states in his article on the blog Climate Audit, the emails in the above captioned time period were not confidential documents and were not in any way scandalizing or controversial. Most were routine communications involving DNCPress, or routine, housekeeping matters dealt with by Jonathan Kaplan. There is nothing in any of the documents that would suggest that Debbie Wasserman-Schultz, who at that time was the head the DNC, deserved to lose her job because of the content of any of those emails. None of them could be used by Russians, or anyone else, to damage Hillary Clinton's Presidential candidacy. There were only 816 emails produced during the entire period., or at least are available in the Wikileaks archive. This amounts to only 1.72 emails per day. Starting April 29, 2016, 26,899 emails will be produced ending on May 25, 2016. This is an mindnumbing increase in daily email volume, from less than 2 emails per day to 739 emails per day. There might be an alternative explanation for this, cited below as a possible DNC email retention policy. The sunami of emails is likely tied to the subject matters of at least two groups of emails. To get a perspective of how this change in volume looks on a graph, the one prepared by Steve McIntrye is available below, and a link to his work about the DNC hack is available in the footnotes. Also following below are the screencaptures of my queries of the DNC emails database at Wikileaks, showing the results.

This chart shows the radical increase in average emails per day at the DNC coinciding with the Crowdstrike engagement to responde to a suspected hack of the DNC. The May 6 date is when Crowdstrike allegedly found Russians were the hackers. The June 10, 2016 date is when Crowdstrike decided to finally contain the hack and get the malware off the DNC network. The chart was prepared by Steve McIntyre, the Webmaster of the Climate Audit Wordpress blog. Mr. McIntyre's article in the blog is my main source for this article in the DNC Network part of the Election Report blog.
Besides a rate of production/receipt of emails by DNC employees, the 1.72 emails per day average during this period might be accounted for when applying any retention policies enforced by DNC management. There was a statement by one of the readers in the comments section of Steve McIntyre's article that the DNC has a email retention policy of 30 days. I have not confirmed that claim; however, such a policy would explain the 1.72 emails per day statistic very neatly, and could also provide information as to when the emails were stolen. If there is such a policy, that emails not be retained longer than 30 days, there had to be exceptions to that policy, as there typically are exceptions in such policies. That would explain why there were only 816 emails still in the system as of April 18, 2016. Why this gives us a clue as to how this can tell us when all of the emails were stolen is the fact that there were so many emails created in the April 19, 2016 to May 25, 2016 period that they would all still be there on May 25, 2016, or the vast majority would be as that would only encompass 36 days. So, only those emails that fit some exception to the DNC retention rules for the first 6 days of that period would still be on the network to be stolen as of May 25, 2016. So, we have another potential finding that helps understand this matter, provided what we read about a 30-days retention policy is accurate. This retention policy would result in a large number of emails being automatically deleted by the system, or the employees would have to do it manually in order to be compliant. In some institutions, employees are only given so much storage space in their email accounts. If they store too many old ones, they can be locked out of their email accounts. Here is the latest finding:
Again, this finding is contingent upon the retention policy being accurate. The last email was stolen on May 25, 2016 at approximately noon because that is the last date on a DNC email in Wikileaks, and the timestamp was at about noon on that email. Sometime shortly thereafter, all the emails dating back to Januray 1, 2015 were swept out in the exfiltration. As the spy agencies like to say, I have "HIGH CONFIDENCE" in this analysis, but there is still a possiblity that the DNC just created 1.72 emails per day, or that the emails were stolen in groups. My opinion is that is unlikely because all of the emails in the Wikileaks archives up to April 19, 2016 represent so few of the grand total of emails in the Wikileaks archives. Therefore, if the retention policy is true, an unknown, but possibly substantial, number of emails were deleted out of those between January 1, 2015 and April 18, 2016. These deletions would be responsible for the few emails in that time period as compared to after April 18, 2016. However, one has to keep a flexible mind. New information is always coming to light concerning the background of this election campaign.
One group of emails in this captioned time period dealt with the Bernie Sanders campaign and the allegations of unfair treatment of Sanders by DNC management. The second involves some strange movements in donations given to Hillary for America, Hillary Clinton's 2016 Presidential Campaign organization. Most of the public already knows about Bernie Sanders and his supporters complaining about bias in favor of Mrs. Clinton by the DNC executives in particular. Some of the emails appeared to support some of these allegations. Much fewer members of the general public know anything about the emails concerning these strange monetary transactions among the three organizations of Democratic Party professionals and employees. That is the more peculiar of the two.
Some donations were sent to Hillary for America, but then forwarded to the DNC, which would, in turn, forward the money to a state Democratic Party committee, such as Iowa's State Democratic Party Committee, just for a hypothetical example. The state party committee would then send the money back to the DNC, which would then send the money back to Hillary for America. Yes, this sounds like a kind of money laundering, and I suspect it is an attempt at precisely that activity. It just isn't a very competent example of it. Some of the people involved became concerned, and email volume rose as inquiries were made about why the money was being shoveled about from place to place.
The time period in which the emails concerning the Sanders allegations, and the movement of money donations, were created is where someone seeking damaging information would have to look to find it. Prior to the April 19, 2016 through May 25, 2016 time period, there were no controversial emails produced by the DNC that would entice any foreign hacker of disgruntled insider to steal them. No one could be blackmailed with the January 1, 2015 through April 18, 2016 emails. Only the emails starting on April 19 had any potential to be used to damage anyone in the DNC or Hillary Clinton's campaign. It should be noted that Crowdstrike was there to protect the integrity of the DNC's data during almost the entire period in question. If all the emails were stolen at one time, on or shortly after May 25, 2016, Crowdstrike could havde stopped them, but chose not to do so. This is important. Crowdstrike chose not to stop the hackers, or the leakers, from stealing the emails. There never was a reason for all of those damaging emails to be stolen by any foreign hackers or internal leakers.
It should also be noted that the Sanders emails had more impact on the early stages of the 2016 campaign as Sanders supporters became disaffected from the DNC executives. The disaffection was the result of the Sanders supporters having access to emails in which Sanders was insulted and attacked by DNC executives. The lawsuit involving Federal Election Commission regulations about the handling of donations is a very recent event, but spurred the curiosity of private researchers and freelance investigative journalists on the Internet, such as Ms. Tracy Beanz of YouTube, Facebook Twitter, and Bit Chute. Ms. Beanz recently completed a comprehensive video about the strange movements of money, and the increases in email volume at the DNC that resulted. An embed of this video follows, along with an embed of an interview on YouTube of Ms. Beanz.
What we know now about the nature of the emails in the Wikileaks DNC Email Archive is the overwhelming number of emails are totally innocuous. They had no value of any kind to any foreign intelligence agency unless such matters as what hotels to stay in, how to get a good seat at the Kentucky Derby, or a documentary on C-Span are important to some foreign power. The FBI's director at the time, James Comey, informed Congress during one of the many hearings about this whole Trump-Russia-Wilkileaks theory, that he had the DNC warned on more than one occasion that they might be hacked starting in the summer of 2015. I can't imagine who would be hacking the DNC for their whopping 1.72 emails a day in 2015, none of which had any kind of salacious revelations about much of anything, yet, that is what we were told in 2017 and 2018. Whoever was after dirt on the Democrats, or through any opposition research on the DNC servers, dirt on the Republicans, would have been very disappointed. Any foreign intelligence service, or disgruntled DNC employee, would have to know there would be a treasure trove of emails created in the brief span of time from April 19, 2016 through May 25, 2016 to obtain anything very interesting. Unless someone writing one of these emails included such a person on the distribution line, either as primary receiver or on a CC list, it would be difficult to know that such emails were being created without access to more than one DNC employee's email accounts.
Next, and hopefully finally for this subject, we will look at how plausible it is that Seth Rich, an employee of the DNC who was shot to death on July 10, 2016, stole the DNC emails and gave them to Wikileaks. After Seth Rich, we will take a look about how likely it is that the Russians spent one year in the DNC network reading 1.72 emails per day, hoping for something interesting. You be the judge.
Note: The two videos of Tracy Beanz reporting her findings from the Wikileaks emails about the movement of donation money through the Hillary Campaign, the DNC, and state Democratic Party committees were sources for this article and are embedded above for reader viewing.
The other sources include the Wikileaks database of DNC emails and query results found in the above screencaptures. Finally, the report by Steve McIntyre in the Climate Audit blog on WORDPRESS accessible through the link below.